Sharing Data (Optional)
Contents
Sharing Data (Optional)#
Overview
Teaching: 30 min
Exercises: 5 min (optional)
Questions:
How do I share my results?
Objectives:
Understand the basics of Identity and Access Management (IAM)
Add collaborators to a Bucket with appropriate permissions.
Security#
Everything in the cloud requires permission (authorization). Let’s first verify that we have the permissions to create a bucket. A Bucket (a resource) is created within a project and inheres permissions from it.
We are interested in what permissions that your account has for your project. To do this navigate to the IAM page (Navigation Menu -> IAM & Admin -> IAM -> Permissions -> View By: Principals). This shows the permissions for the project.
Note: There is a powerful filter box to limit the permissions shown.
You should see a row with your account shown in the Principal column. Here you should see the “Editor” Role in the Role column. A role is a collection of permissions managed by Google or someone else. The Editor, Owner, or the Storage Admin role for a project will allow you to create, access, and delete Buckets in the project.
There are three important pieces of information that work together to form the IAM policy. The permission (role), the identity (principal), and the resource (project). This is another who (identity), what (permission), and where (resource).
Exercise
Answer the following questions:
What is the “Who, What, Where” of the IAM policy that allows you to use your project?
What else has permissions to do things in your project and state the “Who, What, Where”?
Sharing Results#
In order to share resources outside a project we must use the Identity Access Management service. This is a powerful tool to grant and restrict access to resources, and if not done correctly It can have serious consequences. Incorrect permissions can lead to exposure of sensitive data, destruction of data, and authorized use of resources that can result in huge bills. When in doubt, seek help.
The question “What access is really needed?” is the Principal of Least Privilege and is a major cornerstone of security. We need to determine the lowest set of permissions or roles that is needed. In our case we wish to grant the “Collaborator” the “Viewer” access to the “results bucket”. This will allow them to view, list, and download all objects in the bucket. This illustrates that for a resource a member (identity) is granted a permission (think of it in this order). Together this is called a policy. Google also uses “Roles” as a collection of predefined and managed permissions.
What we do not want to do is add the collaborator to the project! This would give them access to all storage buckets and all resources.
We will now add Members to a Bucket using the Web Console. We will use the Web Console to interactively build the policy binding by doing the following:
Navigation Menu -> Storage/Cloud Storage -> Buckets -> Click on the Bucket Name (Bucket Details) -> Select the Permissions tab -> Click Add next to “Permissions” above the permissions list.
In the “New Principals” box add the Identity for the collaborator (another individual) as directed by the instructor.
Select the “Storage Object Viewer” by typing “Storage Object Viewer” in the filter and then selecting “Storage Object Viewer”. Do not use any “Legacy Storage” roles.
Click “Save” to save the policy.
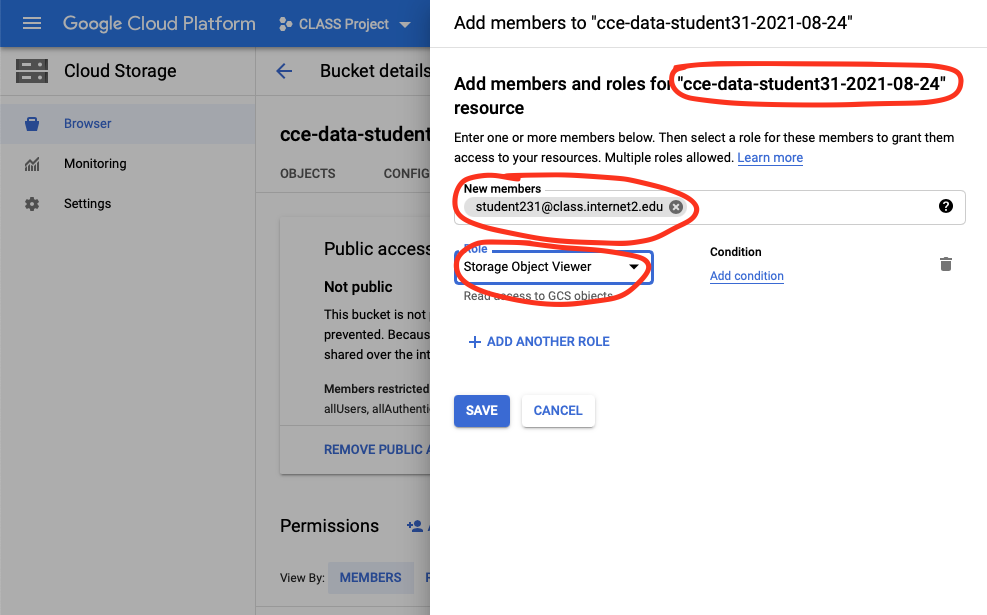
Verify the policy is listed in the “Permissions” table on the “Bucket Details” page (you should now be on this page).
Advanced Note: Changes in permissions will show up on the Home -> Activity page.
Collaborators should now be able to see the contents of the bucket by explicitly naming the bucket. Below shows student321 accessing the bucket (note the prompt).
student231@cloudshell:~ (t-monument-315019)$ gsutil ls gs://essentials-learner-2021-12-17
gs://essentials-learner-2021-12-17/output/
student231@cloudshell:~ (t-monument-315019)$ gsutil ls gs://essentials-learner-2021-12-17/output
gs://essentials-learner-2021-12-17/output/result-LC08_L1TP_025033_20211010_20211018_01_T1.png
gs://essentials-learner-2021-12-17/output/result-LC08_L1TP_025033_20211010_20211018_01_T1.png.aux.xml
Now remove the access by selecting the checkbox on the row with the principal identity and click remove. Now verify that the collaborator does not have access
student231@cloudshell:~ (t-monument-315019)$ gsutil ls gs://essentials-tmiddelkoop-$(date +%F)/output
AccessDeniedException: 403 student231@class.internet2.edu does not have storage.objects.list access to the Google Cloud Storage bucket.
Exercise
Instructors: You may want to have students share these buckets for the example to reduce screen flipping and involve the students.

